 Selasa, 4 Maret 2025 (15:56)
Selasa, 4 Maret 2025 (15:56)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Kubernetes Security | Authenticating Webhook and Authentication Proxy Explained (JMMTechnology) View |
 |
Authenticating Proxy in Kubernetes: Simplified Guide with NGINX and OAuth 2.0 (Distributed Systems) View |
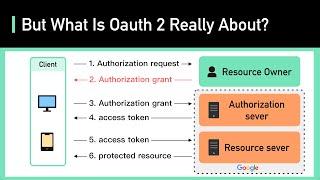 |
OAuth 2 Explained In Simple Terms (ByteByteGo) View |
 |
Kubernetes Security | Authentication Pt1 (JMMTechnology) View |
 |
Kubernetes API Explained (Salman Iqbal) View |
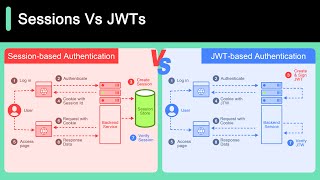 |
Session Vs JWT: The Differences You May Not Know! (ByteByteGo) View |
 |
OAuth 2.0 explained with examples (ByteMonk) View |
 |
Implementing LDAP authorization for Kubernetes through Webhooks - Jordy Ruiter (TheSmartbit) View |
 |
Kubernetes video course 29. Authentication (StudyTrails) View |
 |
How to implement different Kubernetes Authentication Strategies (Middleware Technologies) View |